Active Standby Failover Asa
- Asa Active/standby Failover Check - Cisco Community
- How To Failover Asa Firewall
- Cisco Asa Failover Active Standby
- How Failover Works On The Cisco Secure PIX Firewall
When you enable stateful replication with active/active failover, you significantly reduce the available processing capacity of each failover pair member. Generally speaking, active/standby is the preferred deployment model for failover. Consider clustering instead of active/active failover when your ASA deployment scenario requires load sharing. In this article we will share how to configure Cisco ASA Failover into Active/Standby mode, firstly, assume that your primary Cisco ASA is configured and working. Primary Cisco ASA. Setup your failover interface on Primary Cisco ASA. Failover lan unit primary. Interface gigabitEthernet 0/3. ASA active/standby failover-primary not able to communicate with standby. Guitardave asked on 2009-06-15. Cisco; 11 Comments. There are two different failover modes that are supported on the ASA platform: active/standby and active/active. In this article we will focus only on configuring active/standby failover. In an active/standby failover setup only one unit called the active unit is passing traffic. The standby unit is used as a backup of the active unit and only. Our standby unit in a Cisco ASA Active/Standby cluster failed. I have received the replacement unit from Cisco and am ready to swap out the standby unit. I need to have zero downtime during this swap out. On the replacement unit I have done the following: A) Made sure the software & asdm are on the same version as the active unit.
This post describes how to configure ASA Active/Standby failover.
Identical Cisco ASA firewalls (same hardware, model, interfaces and RAM etc) can be configured for failover, thus allowing for uninterrupted network connectivity. The Cisco ASA supports 2 failover configurations Active/Active (both appliances pass traffic) and Active/Standby (only the active appliance passes traffic, whilst the other appliance is waiting for failure/failover to occur).
The ASA appliances are connected to each other through a dedicated failover link, this can be any spare interface not currently used. Stateful failover can also be configured; this replicates the firewall state information to the standby appliance.
Failover Link – the 2 appliances communicate with each other over a failover link. The failover link can be any spare interface on the ASA.
The following information is communicated over the Failover Link
- Unit state
- Power status
- Hello messages (keep-alive)
- Network Link status
- MAC address exchanges
- Configuration replication and synchronisation
Stateful Failover Link – Is optional if state information is required to be synchronised between appliances.
- Can used dedicated interface for state or share the Failover Link interface
- You could share a regular data interface but NOT recommended
- All information sent over the failover/stateful failover links is sent in clear text, to encrypt this information use a failover key (recommended) – VPN pre-shared keys etc would be transmitted over this link, so secure the communication.
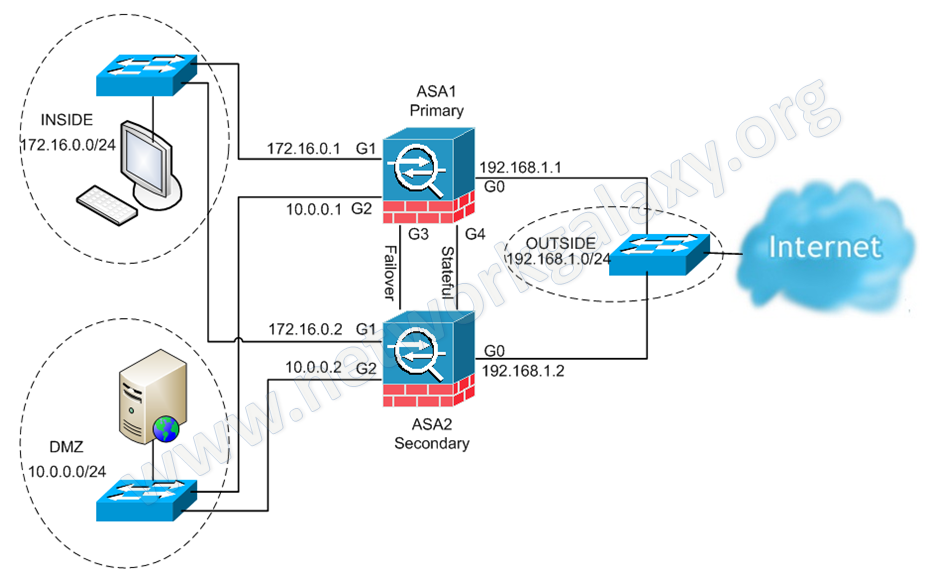
The purpose of this blog post is to document the steps to configure the Cisco ASA firewalls in Active/Standby Failover mode. The Cisco ASAv virtual appliance version 9.5(2) was used in this configuration, refer to the previous post on how to configure ASAv in GNS3.
Active/Standby Failover Configuration Example
Asa Active/standby Failover Check - Cisco Community
Configure interfaces
Configure the INSIDE and OUTSIDE interfaces with the Active and Standby IP address
Un-shutdown the interface used to be configured for failover
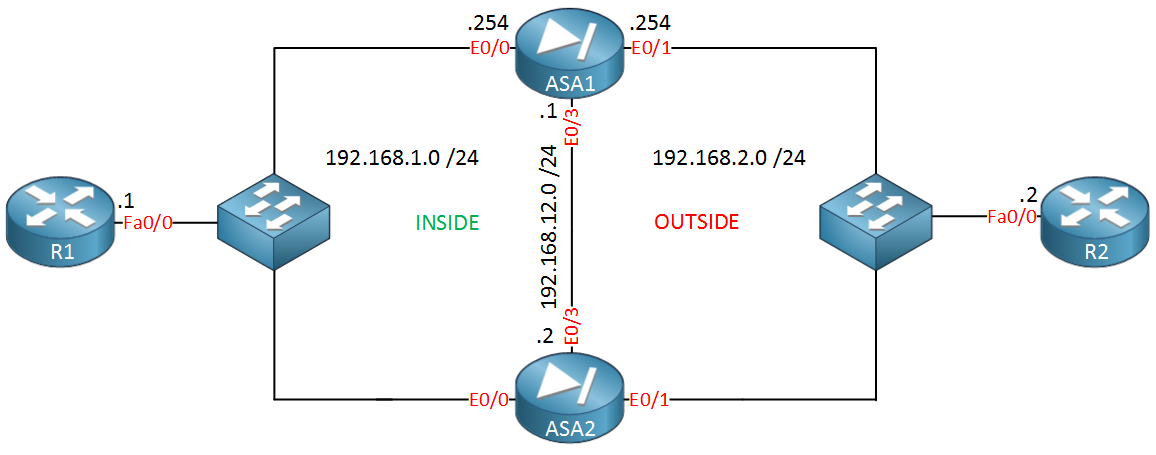
Configure failover interface called “FAILOVER” on Gig0/2
Configure IP address on the Failover Interface
Configure a Failover Key (to ensure traffic is encrypted when sent between devices)
Configure the Firewall as either Primary OR Secondary (NOT BOTH)

Step 6 – Enable Failover on the Firewall
Configure Stateful Failover Interface
Configure Stateful Failover (notice we are sharing the same interface for both Failover and Stateful Failover)
Use the same commands on both appliances, but ensure to specify “failover lan unit primary” only on the preferred Primary/Active appliance and specify “failover lan unit secondary” on the preferred Secondary/Standby appliance.
Verification Commands
Using the command “show failover” will display information on the failover state of the local appliance, such as whether Failover is turned on, Failover Priority, Failover Interface, Timers, State (local), State of other host etc
If Stateful Failover is configured it will show Statistics
The command “show failover history” will tell you what events occurred and when
Additional Useful Commands
Use the command “prompt hostname priority state” to display on the console the Priority and State of the firewall you are connect to
How To Failover Asa Firewall
Entering the command “failover standby config-lock” will stop configuration of the cluster from the standby appliance.
To manually failover to the secondary appliance you can use the command “no failover active” from the current Active firewall or if on the Secondary firewall use the command “failover active”. In the screenshot below, notice after the Active firewall was configure not to be active the prompt changed from “act” to “stby” to confirm this appliance is now the Standby firewall.
Full Configuration
Cisco Asa Failover Active Standby
Primary Firewall
How Failover Works On The Cisco Secure PIX Firewall
Secondary Firewall
